MITM Attack in LAN (Demonstrated by FB Hacking)
Today we will learn how to use ARP Spoofing and Phishing to perform MITM Attack.
Address Resolution Protocol (ARP)
Do you guys know what is a LAN? Well “A group of computers which share a common Internet connection is called Local Area Network.” So if 3 computers use the same router they are in LAN.But there is something interesting about LAN, when two computers in a LAN want to connect to each other then IP Address is not sufficient, we need MAC Address too. But as I told you before that when a data packet is sent it contains IP Address and Port number but not MAC Address. So how they can know MAC Addresses of each other? Well that’s where Address Resolution Protocol comes into play.
Lets imagine two computers A and B are in a LAN and Computer A wants to connect to Computer B so can A connect directly to B? No. They have to verify if this is the same computer they want to connect to.
Lets see how it works:
1. Computer A sends an ARP request its like asking “Hi! I was looking for computer with IP Address 192.168.42.4 and I think thats you! And it looks like we are in a LAN so can you please tell me whats your MAC Address?
2. Computer B sends him a confirmation like “Yeah bro! That’s me and here is my MAC Address”.
3. Computer A “Yeah now we can establish a connection” and then Computer A builds a cache where it can store the MAC Address of Computer B so that it can connect faster next time.
This is what ARP does, it asks for MAC Address before connection if the target computer is in LAN.
Man In The Middle (MITM) Attack
So as wikipedia says:
Man-In-The-Middle attack is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other.
Confused? In this tutorial you will see and learn.
So we will do it in three phases:
1. Preparation for Phishing
2. ARP Spoofing
3. MITM
Note: I am using Kali Linux which has setoolkit (Social Engineering Toolkit) and ettercap preinstalled, so use google to know how to install these tools in your machine.
And if you are a Windows/Mac user then you can use google to get directions on how install Linux. *Savage*
So let’s go
Phishing
In phishing, the hacker creates a webpage(s) to steal sensitive information from the victims. For example if I create a website and claim that it can hack facebook accounts and all you have to do is to enter your facebook username and password and then choose the friend you want to hack. Stupid people will get super excited and will enter their username and password and guess what…I will get their facebook username and passwords.
LOL its so easy and its called Phishing.
Setting up our Fake Facebook Website
Open terminal and type “setoolkit” and a window like this one will open
Just enter 1 and press enter, now you will get the following options.
Now press 2
Now enter 3 and you be greeted with these options.
Now an another window will open, and all you have to do is to enter your IP Address (to find your IP Address enter ifconfig in terminal) and after you enter your IP you have to enter the website you want to clone and in this case it is facebook.
Now the apache server should be running and everyone who will visit our “IP Address” will be redirected to our “Phishing Facbook Page”
Now lets move to next step.
ARP Spoofing
With ARP Spoofing we can redirect the LAN users to our desired website without them knowing.Like if they want to go to google.com we can redirect them to facebook.com
Note: I am using gedit, you may replace gedit with your text editor like leafpad or VIM.
1.Setting Up The Ettercap Configuration File
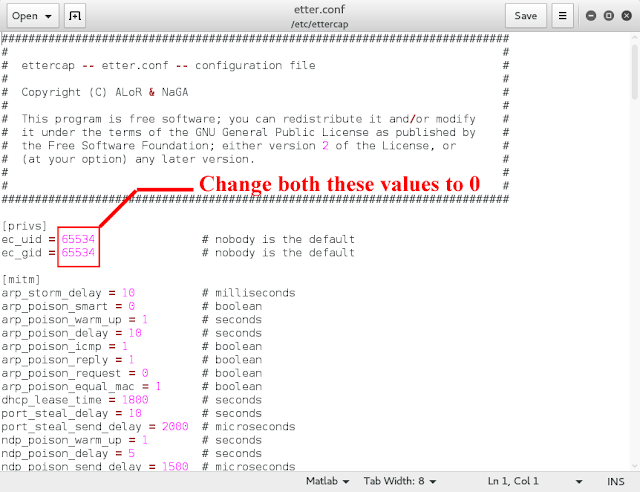
Open terminal and type “gedit /etc/ettercap/etter.conf”You will be greeted with a text file like this one:
As this is not yet another hacking blog so you don’t have to follow the procedure blindly. Well these two lines are meant to configure who should be allowed to use this configuration file and “Nobody” is the default. Now, we changed it to 0 and that means we gave the permission to the root user.
Now go to end of this document and make the following changes:
Removing them means we want to activate the commands next to it.
Now save this file and move on to the next step.
2. Enabling IP Forwarding
Open terminal and type “nano /proc/sys/net/ipv4/ip_forward” and you will be greeted will a screen like this:There is nothing except a 0 in this file and you have to change it with 1. So why we used nano instead of gedit? Well we are trying to edit a locked file and we can’t overwrite it with gedit. So we are using Nano, the text editor of Linux 0 means no and hence in this case it means no ip forwarding. We will change it to 1 (yes) because we want to use ip forwarding.
So yeah, change the 0 with 1 and press Ctrl+o (it will overwrite the file) and then Ctrl+X (to exit the console.
Now in terminal enter “gedit /etc/ettercap/etter.dns”
Another text file will appear and in place of Microsoft stuff you have to make the following changes:
Great!
Now open Ettercap and click on Unified Sniffing as follows:
Now you will have to choose your interface. TIP: Open terminal and enter “route” whenever you need to know your interface name.
Now scan for hosts as follows:
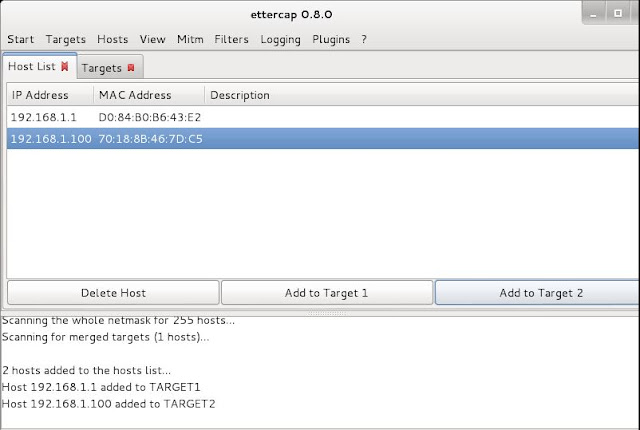
Now open the host list:
Now add the users you want to hack to targets.
Now proceed as shown below,
That’s all, Now when your victim will enter www.facebook.com, he
will get your Phishing Page instead of the Real Facebook. If he enters
(he wiil) his username and password, they will be saved in a text file
under the folder “var/www/html” of your computer.
Note:
If you don’t want to “Hake” facebook and want to redirect users to your custom page then you can put your custom page in the place of var/www/html/index.html.
And in the step you edited /etc/ettercap/etter.dns file, you used your IP. So you can write a website name you want redirected and then add IP Address of your desired site in front of it. So if you understand the basics, you will know the possibilities are countless.
If you don’t want to “Hake” facebook and want to redirect users to your custom page then you can put your custom page in the place of var/www/html/index.html.
And in the step you edited /etc/ettercap/etter.dns file, you used your IP. So you can write a website name you want redirected and then add IP Address of your desired site in front of it. So if you understand the basics, you will know the possibilities are countless.
Well I think its enough for now and someday we will make another tutorial on MITM.
Till then, Good Bye.
./logout






















ReplyDeleteMy life was falling apart, I was being cheated and abused, I had to know the truth and needed proof. I contacted a private investigator that linked me with onlineghost who took care of the hack job. He hacked his iPhone,Facebook,Instagram, Whats app, twitter and email account. I got all I wanted as proof . I”m glad i had a proven truth he was cheating . Contact him for any hack job. Tell him i referred you to him, he will surely meet your hack need. Contact: onlineghosthacker247@ gmail .com
Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com